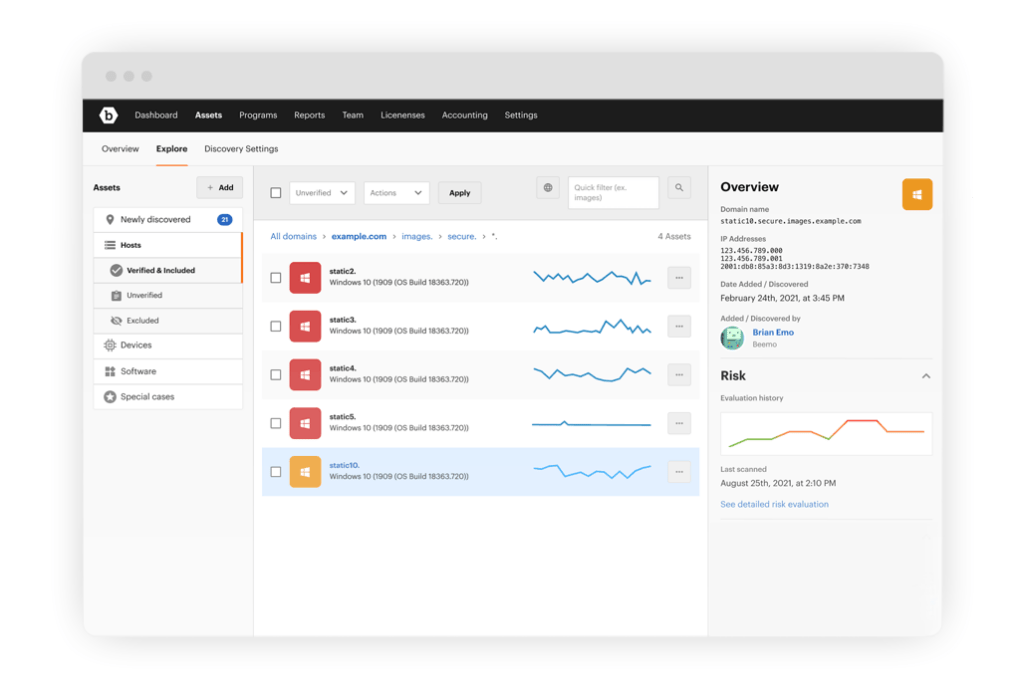
See and manage everything
Inventory and manage assets, and find hidden ones that scanners miss–exactly as an attacker would.
Assign and prioritize risk
The Bugcrowd Platform’s AssetGraphTM technology ranks asset risk based on a rich repository of security knowledge based on data collected over a decade.
Analyze and report
Analyze results and package them along with recommendations for executive review—highly useful during M&A!
Pivot to remediation
Easily transfer discovered vulnerabilities into Bug Bounty or Pen Test solutions for remediation.
Power of the Crowd
Going beyond automation
A third of successful cyberattacks now occur via unmanaged or unknown assets. Bugcrowd Attack Surface Management solutions drastically reduce that attack surface by activating a global network of trusted security researchers with deep recon skills. We then augment and guide their work with automated workflows—rather than solely relying on scanners which only help you find assets that attackers knew about yesterday. In short, Bugcrowd helps you discover vulns that threat actors haven’t found yet.
BUGCROWD PLATFORM
Don’t get blindsided by unknown attack vectors
The Bugcrowd Platform helps you continuously find and fix critical vulnerabilities that other approaches miss.
Working as an extension of the Bugcrowd Platform, our global team of security engineers rapidly validates and triages submissions, with P1s often handled within hours
The platform integrates workflows with your existing tools and processes to ensure that applications and APIs are continuously tested before they ship
We match you with the right trusted security researchers for your needs and environment across hundreds of dimensions using machine learning
Our platform applies accumulated knowledge, from over a decade of experience with 1000s of customer solutions, to your assets and goals to optimize outcomes
Built-in security workflows streamline program on-boarding, promote customer and researcher communication, and expedite vulnerability triage, validation, and remediation activities
Shift Left: Flow findings directly into your SDLC

Get started with Bugcrowd
Attackers aren’t waiting, so why should you? See how Bugcrowd Attack Surface Management can quickly improve your security posture.